How to know the secrets of a website server?

A website presents itself as all its information is public. However, there’s is an ocean of useful data hidden which isn’t visible to the public they target. It’s only visible to people who peep into the website’s server details. This is the next step after you have passively collected information about your target individual/organization.
Have you completed the last to-do? Complete that before proceeding ahead. Don’t forget to share your interesting finds in the comments. In this article, we’ll learn about finding server details. It’s time to interact with the server now!

How to see website server details
It’s not that straightforward. Obviously, no one would want their website server details to be displayed in the news. It’s a game of the combination of acquired skills, your observation level, the defense of the target, and patience. These things will be required in every step in your penetration testing indeed.
To know about a website, you’ll need to know what’s going on inside it.
1. Gather passive information
First, find information about the target without directly interacting with it. Use this article for collecting information passively. Meanwhile, don’t forget to try Google Dorking.
2. Know about the subdomains
Second, know about the subdomains of the domain. Gather all the subdomains you can find and note them down and try Google Dorking on them.
3. SSL details
SSL stands for Secure Socket Layer. It helps in encrypting communication over the internet. A website gets served on HTTP(port 80) or HTTPS(port 443). In HTTP, it’s easier to sniff the network and sensitive information will be out. That’s why mostly live websites on the internet use HTTPS. There are 2 versions of SSL — SSL 2.0 and SSL 3.0. Kali Linux has a great tool — SSLSCAN to capture details about the SSL of your target. Open terminal and type:
sslscan yourtarget4. DNS Enumeration
DNS enumeration is to find information about a server, for example, the IP addresses, server names, records, etc. To illustrate this, we’ll try out a tool called Nslookup and find out nameservers and mail server records of facebook.com.
Finding MX records:
- Issue the nslookup command in terminal
- Issue the following command: set type=mx
- Next, enter your target domain
This is how it will look like:
haox@haox>nslookup Default Server: UnKnown >set type=mx >www.msn.com Non-authoritative answer: www.msn.com canonical name = www-msn-com.a-0003.a-msedge.net www-msn-com.a-0003.a-msedge.net canonical name = icePrime.a-0003.dc-msedge.net icePrime.a-0003.dc-msedge.net canonical name = a-0003.dc-msedge.net dc-msedge.net responsible mail addr = msnhst.microsoft.com ----> This is required data serial = 2016090201 refresh = 1800 (30 mins) retry = 900 (15 mins) expire = 2419200 (28 days) default TTL = 240 (4 mins)Finding Names servers:
- Issue the nslookup command in terminal
- Issue the following command: set type=ns
- Next, enter your target domain
This is how it will look like:
haox@haox>nslookup Default Server: UnKnown>set type=mx >www.msn.comNon-authoritative answer: www.msn.com canonical name = www-msn-com.a-0003.a-msedge.net www-msn-com.a-0003.a-msedge.net canonical name = icePrime.a-0003.dc-msedge.net icePrime.a-0003.dc-msedge.net canonical name = a-0003.dc-msedge.net dc-msedge.netprimary name server = ns1.dc-msedge.net ----> This is required data serial = 2016090201 refresh = 1800 (30 mins) retry = 900 (15 mins) expire = 2419200 (28 days) default TTL = 240 (4 mins)5. Detecting Load Balancers
Load balancers are a way to distribute the load upon other servers. This is done to make the applications work effectively and maintain uptime. For example, if you would run host www.google.com, it will resolve into multiple IPs.
www.google.com has address 142.250.194.68 www.google.com has address 142.250.186.132Load Balance Detector(LBD) is a bash script in Kali to detect if there’s a load balancer or not and this is how it works:
haox@haox>lbd www.google.com Checking for DNS load balancing: NOT FOUND Checking for DNS load balancing: gws NOT FOUND www.google.com does Load-balancing. Found via methods: HTTP[Diff]If detected, next you would want to know the real IPs behind these load balancers. For this,
- Download Halberd tool
- tar xzvf halberd-0.2.4.tar.gz and navigate inside
- python setup.py install
- Halberd stackoverflow.com and output will look like this
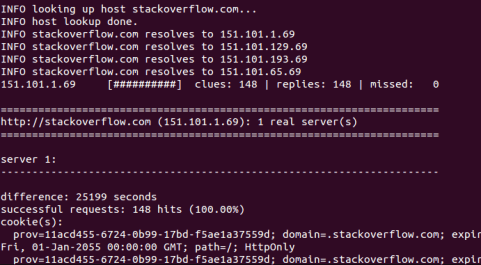
This way you can find a lot of details about a website server. There are many more techniques and we’ll cover them in the upcoming articles, comment below the techniques you want to see in the next article. When you’ll try what is shared above, you’ll get a feel of pentester! Keep brewing that feeling with caution.CAUTION: You need to make sure that you will not use this information for any illegal purposes. This information is being shared for educational purposes only. If you find something sensitive while practicing this, do not use that information instead inform the website owner as soon as possible.
Here’s your TO-DO:
- Complete the last articles if you missed them
- Practice the above techniques
Keep practicing till the next article which would be on bypassing Cloudflare(this is gonna be bomb) and don’t forget to subscribe to get new content every weekend in your email, if you found this interesting.
Originally published at https://haox.hapot.in on October 18, 2021.