The 5-Minute, 5-Step ways to exploit SMTP
The secret I’m going to tell you about is — “Control is an illusion”. The topic( SMTP exploit) will also convince you on agreeing to this quote. Have you covered the basics of remote exploitation we discussed in the last article? If not, complete that first because this is the continuation of it. SMTP is used for sending emails and is the one that doesn’t have any security implemented.
A while back in the roadmap, I had shared the ways to enumerate with SMTP. Now, we’ll talk about how to check if it can be exploited and then exploit it. Are you ready?

Prerequisites
- Do a quick scan of your target, say example.com using nmap to check if your target’s status with SMTP. The response will be something like this.
nmap -p 25 --script=smtp-commands example.com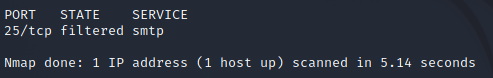
- This will work only if the port will be accepting connections, i.e., STATE in the above step is open. If it’s open, now check for connection. If it succeeds, we can move ahead to try this.
Btw, if you have not subscribed to the newsletter yet, do it now. Such content will keep on adding to the roadmap.
Ways to exploit SMTP
Telnet
The telnet way is the way where we’ll target the mail servers to spoof the emails. TELNET is basically used for checking connection with remote and issue some kind of commands on it. We would use it here as penetration testers to spoof.
Let us check for the connection to open and then we’ll move ahead to spoof
telnet example.com 25Once you type this, it will try to connect to the mail server of your target on the specified port, which here is 25. If it connects, you’ll find the output to be something like this:
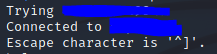
Now, you’re ready to spoof the email.
- TypeHELOand press enter. You would get a pingback.
- Next, type MAIL FROM:[email protected] and press enter. You would get “sender ok” in reply.
- Now, type RCPT TO:[email protected] and press enter. You would get “recipient ok” in reply.
Add subject if you want. SUBJECT:<your subject> and press enter. [OPTIONAL] - Now, type DATA <your email body>.
- Finally, type . and press enter. You would get “250 Mail accepted” in reply.

This is it you’ll get a spoofed email on your receiver’s end. Type QUIT and it will bring you out of TELNET. Now, let me explain to you these terms HELO, RCPT, DATA.
- HELO — This is the first text sent in telnet to greet the server.
- MAIL FROM — This is the sender’s email address from which you want to spoof the emails
- RCPT TO — This is the receiver's email address to whom you want to send an email
- DATA — The body of the message you want to send.
Since we have covered this in the last articles, I’ll leave that on you to explore how to use these for brute-forcing on SMTP. In this way, you’ll need some Google Dorking and other ways to find out emails to break the authentication of those emails. Here is the list of ways to find about the target.
So, you see SMTP is one of the corners where if you find the way to reach it, you can damage it badly. This is the reason why it is required to set SPF, DKIM, and DMARC for a domain(read about these here). Well, this was it for SMTP but this is not the end of remote exploitation. If you know any other way than these for exploiting SMTP, do share in the comments below. Don’t forget to keep practicing side by side, if you are facing some issue, let me know in the comments. Here’s your TO-DO:
To-Do
- Try the above techniques.
- Explore SMTP with Hydra
and don’t forget to do this with caution:\
CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes. If you find something sensitive during the practice, report it to the concerned person immediately.