How to use Metasploit to save tons of time

Metasploit is a powerful tool that is used by ethical hackers to find vulnerabilities on networks and servers. It helps to find the weak spots in the network. I know, how eager you are to know about this tool.

Have you completed the rest of the articles on remote exploitation? This will be the last part of it. Make sure to complete them first, if you’re following the roadmap. Load your guns and let’s complete this.
What is Metasploit?
Metasploit is open-source software whose work is to give you the weaknesses of a system documented in a report. It provides you:
- Payloads: Set of malicious code
- Exploits: Checking existing vulnerabilities in the target
- Post-exploitation code: Test penetration in depth
- Shellcode: Execute script inside the target
and the list continues.
Metasploit step-by-step
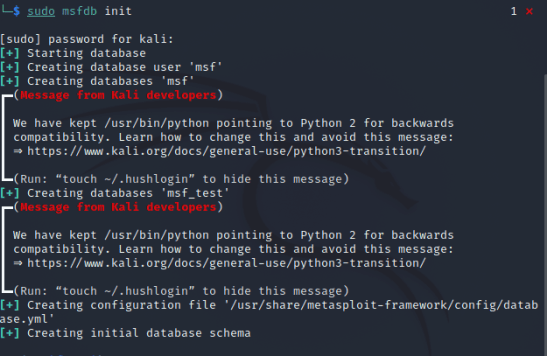
1. Initialize
Run this command in your Kali terminal and it will initialize the database. It uses PostgreSQL as its database. Your terminal will look like this:
2. Run Metasploit
msfconsoleNow, type this and it will start Metasploit. If you want to see commands add -h with it. Let’s check if it’s connected to the database.
db_status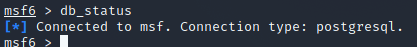
3. Core Commands
Let’s learn what can we do inside Metasploit.
- help — to find a way if you get stuck somewhere
- search — used for searching
- use — if you want to activate some module
- info — if you want to view information about the selected module
- connect — to connect you to the target
- set /setg- set a variable/set a global variable
- get — get a variable
- unset — changing the value of a variable to null
- spool — to output console’s content into a file
- save — save your state of Metasploit so that when you can back, you can resume working
4. Modules
This is all you can do with Metasploit.
- exploit — contains the code exploits
- payload — contains shellcodes for exploits
- auxiliary — verifies if the target is exploitable
- post — destroying target after exploiting (stimulation obvio :P)
- encoder — helps in exploiting encoded content
- NOP — deals with buffer overload attacks
- load — loads different modules
5. Let’s try it out
- It will run what you do with nmap
db_nmap -sV <target-ip>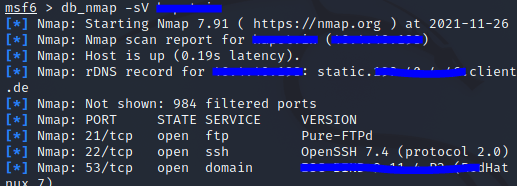
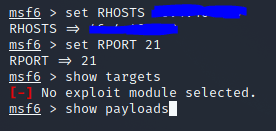
- Exploiting a system:
First, we need to set details inside msf.
set RHOSTS <target ip> set RPORT <target port> show targets -> this will show you the target hosts show payloads -> this will payloads and scripts after exploiatation exploit -> run testThat’s it. Metasploit will itself test the target. This is what this will look like:
Remember, the objective of these articles is to make a path for you, that’s why we started this roadmap. These articles will provide you with information for putting a step ahead. It’s on you to dive in deep into these steps.
Here’s your To-Do:
To-Do
- Try out Metasploit.
- Learn more about techniques for using this tool.
Here we have reached the end of the remote exploitation topic on the server-side. This isn’t the end of the roadmap yet. In the next, get ready to go towards the client-side. Keep practicing and stay tuned with caution.CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes. If you find something sensitive during the practice, report it to the concerned person immediately.