Time can tell your password

Until now, you may have heard of various kinds of attacks to break passwords. The stars of this password attacks industry are brute force attacks and dictionary attacks.
Let me introduce you to the hidden star: Timing based attack
This is a vulnerable code:
def check_password(password):if(password==='My password'):return Trueelse:return False
This piece of code looks great until observed closely. The flaw may not be realised instantly. This script will match the length of the passwords, then it will match the password letter by letter and as soon as there is a difference in password, it returns False.
How does timing attack work?
If I was to guess the password of any website by brute force, it would have taken lots of combination. A 9 character password would have 10⁹ combinations. This is where a timing attack makes its way.
My first guess to try for 9 character password would be 000000000. After this, i’ll try a00000000 -> b00000000 -> c00000000 and so on.
Say, the time took for guess a password was:
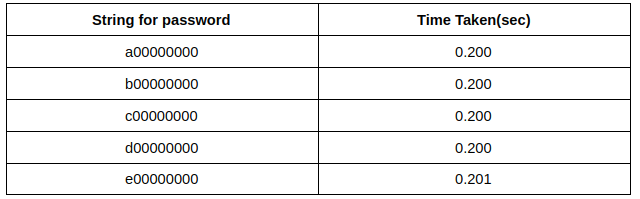
At e00000000, it took a little longer. This happened because the first character had matched and it took a little longer to return False. Hence, the attacker knew the first character is correct.Now, the next guess will be ea0000000.
The difference in the time to return password may be negligible for us and when captured through the network, it gives an idea. The more time it took for the network call to return, the better was the password guess. Yes! now even microseconds will matter. Would this attack be slow? Even if it comes out to be 5,000,000 requests, it can be completed in less than a week.
Timing attacks are a way of exposing the algorithms and complexity of passwords.This can be applied to the algorithms that have time variations in return based on data. Many algorithms like RSA, hash_equals in PHP are vulnerable to this attack.
These attacks are often overlooked during the development phase and if found can release a lot of information like password, algorithm, CPU, cryptographic system design. This attack takes some planning and analysis, but if succeeds, the result can be pretty horrible.
It’s prevention time
The basic idea is to ensure to not let the execution time of the call to make a pattern. For eg:
Instead of using quick exit approach for sign-in
IF USER_EXISTS(username) THEN password_hash=HASH(password) IS_VALID=LOOKUP_CREDENTIALS_IN_STORE(username, password_hash) IF NOT IS_VALID THEN RETURN Error("Invalid Username or Password!") ENDIF ELSE RETURN Error("Invalid Username or Password!") ENDIF
Try this
password_hash=HASH(password) IS_VALID=LOOKUP_CREDENTIALS_IN_STORE(username, password_hash) IF NOT IS_VALID THEN RETURN Error("Invalid Username or Password!") ENDIF
Whatever encryption you’re using, check what time it takes to return after password matching. If it varies, it can be vulnerable. Sometimes, being fond of === can kill too.
Additional protections can be added like CAPTCHA, rate limit. These protections don’t have to do anything with timing attacks. These will help out in increasing security.