How to use Wireshark to capture and monitor packets?

In the last article, I had shared after this article you’ll master LAN sniffing. I hope you have tried your hands on the techniques shared in it. Then, let’s go and learn.
How to use Wireshark?

Wireshark is an open-source packet analyzer that can be used to capture, filter, and inspect the network.
What is a packet?
A packet is a unit of data that is transmitted over a network between the source and destination hosts. These packets are of small size and can be viewed in Wireshark.
Uses of Wireshark
Wireshark can be used in various ways
- Network security engineers use it to examine security problems.
- Users can watch traffic over the network
- One can troubleshoot latency issues and monitor malicious activities
- Analyse dropped packets
Installation
If you have Kali Linux, this will be pre-installed. Otherwise, you can follow these steps:
- Open your web browser and open this link.
- Select and download the installer as per your system configuration.
- Once downloaded, open the software and follow the installing instructions
- Wireshark is ready to use
By now, I hope you have cleared your network basics, if not complete that first. Now, it’s time to visit the interface.
A quick overview — how to use Wireshark?
Let’s learn how to capture plain text passwords in Wireshark (Don’t get serious this is just an example :p).
Step 1: Launch Wireshark and click on the Capture button at the top and choose the network you would like to sniff.
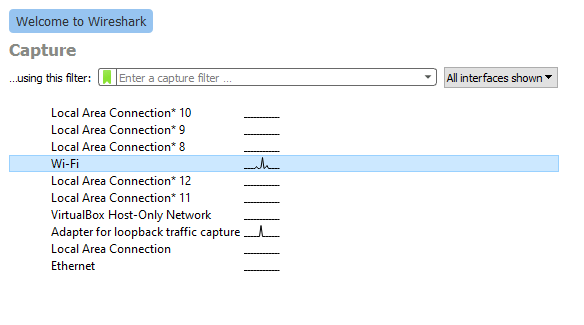
Step 2: Your interface will look like this. Wireshark will start to capture all packets across the network. Now, from your target machine log on to a website that has HTTP authentication.
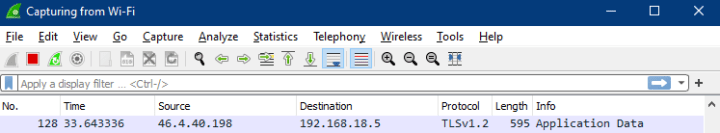
Step 3: Since there are so many packets, we need to filter out packets of our interest. Inside the filter tab, type http.request.method==POST to see only POST on HTTP requests.
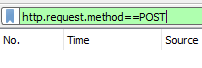
Step 4: Now, log in from your target machine. Your required packets will list down. Right-click on the packet and click on Follow the TCP stream. This will show you the original post request from the victim’s browser. The output will be something like this:
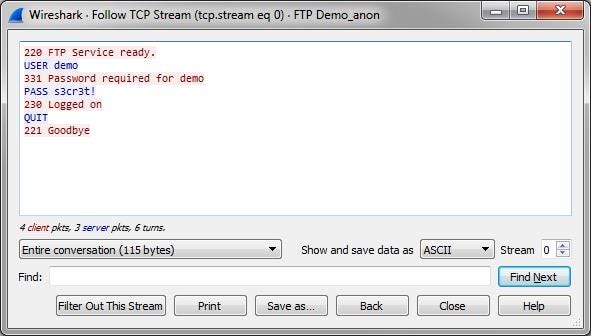
Here user and password are visible clearly. If your target is using an encrypted protocol, you can use the following ways:
- Decrypt traffic with the “Session Keys log” file
Since the target is using HTTPS, it will not be possible to decrypt the request. So, you will have to get their session key somehow. For this, you can follow this. - Decrypt traffic with the private key of the webserver
In this, you’ll have to decrypt the traffic by decrypting the access to the private key of the webserver, which allows you to decrypt all connections to that server. We’ll learn about this at a later stage.
This is an example of how to use Wireshark, there are more you can explore. There are various filtration methods, graphs. Don’t forget to visit them, this blog will help you in learning in-depth.
Remember to do this with caution:
CAUTION: This information is for educational purposes only. Do not use it for any illegal purposes.
Next, we’ll learn about remote exploitation. Keep practicing till the next and here’s your to-do:
To-Do
- Try out Wireshark
- Combine Wireshark with the techniques in the last article
If your memory is like mine, you would need a reminder when I post :P. So, let me remind you when I post.